Why choose Panoptica?
Four reasons you need the industry’s leading cloud-native security solution.
In this post, we discuss what an attack path is, how mapping an attack path works, and how it can help you get improved visibility into your cloud environments to better identify potential critical risks and vulnerabilities.
An attack path is a visual representation of the path that an attacker takes to exploit a weakness in the system. An attack path focuses on looking at the entire context of related risks and security issues to see and address the potential weaknesses.
An attack path is important to prioritize critical potential risks in cloud environments. The attack path offers the ability to look at cloud environments from the perspective of the attacker - hackers are constantly seeking pathways, preferably those of least resistance, to compromise a system by exploiting its vulnerabilities.
With today’s general awareness and concerted effort towards cybersecurity, cybercriminals rarely ever find a single gaping loophole or a silver bullet through which an entire enterprise system is compromised. Instead, they often capitalize on a series of vulnerabilities that successively lead them to discover an exploitable path to confidential assets.
Attack paths are helpful as they visually highlight the connected attack vectors available to cyber attackers as they probe for weaknesses in a system that could result in a data breach or stolen credentials.
Terminologies are important, especially when they form part of the nucleus of a solution. It is therefore imperative to understand what differentiates an attack vector from an attack path.
As mentioned earlier, an attack path identifies the vulnerabilities—in a visual form—that an attacker can take advantage of in order to gain access to one or more assets and move laterally inside the compromised network. Beyond visualization, attack path analysis is a set of graph algorithms based on certain graph patterns, generating the most critical path for a certain asset, based on several risk factors that meet a minimum score threshold.
An attack vector is a method used by an attacker to take advantage of a security mishap existing in a system, or a cloud environment.
An attack surface is a much broader term that describes all of the potential vulnerabilities to which your environment is susceptible. It is the entire area of a company’s infrastructure that’s susceptible to cyberattacks.
To protect their assets, it is vital for companies to understand critical and vulnerable routes in their network where there is potential for exposure and exploitation by nefarious actors. Organizations need to have both the visibility and ability to defend their environment. They need to proactively retrace the footsteps and potentially pathways an adversary would go about subverting their internal network.
Therefore, a business needs to understand how an attacker might gather internal information as stealthily as possible to further burrow into their network using vulnerabilities like insecure passwords, unpatched domain controllers, and unencrypted protocols.
Attack path analysis helps organizations to model how a hacker would likely attack them. An attack path analysis sheds light on an organization’s most valuable assets and identifies how to optimally secure them by reducing their exposure to cyberattacks.
Discovering attack paths is also crucial for highlighting the possible sequences of a system’s exploitation. Most attackers typically follow a simple, yet regimented multi-attack process that commonly includes the following:
These aren’t linear steps but are often used iteratively as the attacker goes back and forth refining methods for optimal success. This is because attackers often leverage interdependencies among the vulnerabilities it has discovered.
Attack paths often create links to software entities where no direct connections exist, since they reflect chains of abusable user behavior and privileges that surreptitiously generate direct and indirect unintended connections. Microsoft Active Directory and Azure Active Directory notably provide control path environments where attackers can leverage hidden and unintended relationships to launch identity snowball attacks.
Attack path mapping is especially useful when an attack path encompasses multiple behaviors and corporate assets. The mapping shows the process flow of several different vulnerabilities.
Mapping an attack path requires understanding an organization’s attack surface and the assets contained in its system and network infrastructure. Risk evaluation requires mapping the corporation’s digital assets, including cloud-hosted entities with potential attack paths.
The best way is to use topological maps to evaluate likely attack paths and nullify them before an attacker can exploit them. Security teams find it convenient to use graphs to contextually map all the possible paths an attacker can leverage at scale.
Unlike traditional relational databases, which focus on the relationship between tables and the columns of data stored in them, graph databases reference relationships between data points.
The building block of assets in a cloud environment like services, storage, data, networks, and identity are interrelated and dynamically interwoven. Their connectedness and constant churn in a rapidly evolving threat landscape require a real-time vulnerability assessment that addresses this dynamic nature.
However, most traditional cybersecurity solutions consider each attack path as an independent attack scenario. Unfortunately, vulnerabilities that appear insignificant in isolation may become critical when a hacker exploits a sequence of related vulnerabilities.
Graph theory represents the best attack path modeling to help identify critical nodes in a cloud network. The first step on the road to building a graph-based algorithm requires mapping a realistic, cross-domain, and risk-assessed attack path that encompasses the entire cloud enterprise.
So, cloud mapping is the first step in assessing relationships between cloud assets. Cloud mapping provides well-needed visibility that enables DevSecOps to gain a deep understanding of their system's architecture. This, in turn, deepens risk management capabilities by identifying the critical attack paths exposed, along with a clearer view of how to mitigate their attendant risks. Continuous mapping is required due to the huge churn and dynamic movement in assets and entities in a cloud environment.
DevSecOps need to ask pertinent questions to create a unified view through link mapping. This is because links aren’t created in isolation; they have two properties relative to each other: their spatial direction and complexity.
So, the first question is a fundamental one: “Is an asset, A, connected to asset B, and vice versa?” If the answer is affirmative, the next question will explore the complexity of that relationship; for instance, how asset A is exposed or attached to asset B.
The linking process should be flexible enough to accommodate assets regardless of the origin of their platform, whether its from a Kubernetes cluster or an AWS load balancer.
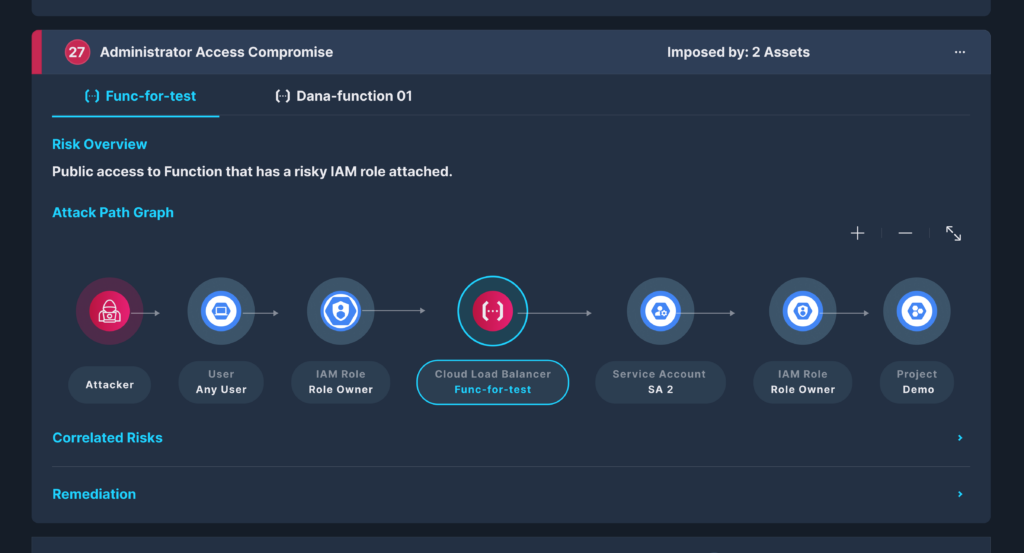
Graphs subsequently use these mapped relationships to create a three-dimensional view of your cloud infrastructure. To build a well-defined graph, a precise relationship table that highlights all the possible links between assets must be created. This table must source data across the domains critical to providing a practical, end-to-end model of attack paths.
However, traditional relational database management systems (RDBMS), with their simple mapping of rows and columns, are insufficient for the task of depicting the cloud graph frenzy. Instead, graph databases, with their more sophisticated structure, needs to be adopted.
Graph databases are designed to store massive graph structures. They are equipped with nodes to store entities and edges to capture the relationship between them. Furthermore, relationships are first class citizens in graph databases, making them a rich resource for quickly transversing data models in cloud architectures.
A prime example is a graph platform like Neo4j, which possess a detailed graph management layout, along with data science library for improving an organization’s network security posture.
Done correctly, the end result should produce a topological view of a well-defined graph that contains relevant cloud entities with nodes and edges representing logical relationships needed to fully identify vulnerabilities.
The attack graph subsequently produced should provide the security teams with all the possible paths throughout their system that culminate in a state where an intruder has achieved his nefarious goals.
Attack graphs are necessary to compute the potential attack paths from both the system's known vulnerabilities and its configuration. Used in conjunction with risk assessment, an attack graph provides security teams with the relevant information to protect their systems and network infrastructure from cyberattacks.
Attack graphs are valuable in helping cybersecurity teams to understand and evaluate the security of an organization’s network, providing them with the insight to analyze and predict an attacker’s behavior.
An attack graph typically contains a series of paths, with each path denoting a series of exploits or atomic attacks. Therefore, penetration testers can use attack graphs to simulate the possible paths an attacker will use to breach a network.
Since cloud environments typically contain a multitude of building blocks, attack graphs are useful for modeling a global view of an organization’s network. In addition, well-tuned graph algorithms in platforms like Neo4j GDS library can be leveraged to reduce cybersecurity risk through advanced threat modeling.
The dynamic environment encountered in today's cybersecurity systems, with the constant change and churn in apps, APIs, endpoints, and software components, located in different parts of the IT value chain, has made it impossible to analyze events or incidents in isolation.
As a result of this dynamic risk environment, there needs to be an approach that suitably accounts for highly parameterized and noncircular attack paths.
Graph theory presents the best approach to sift through and analyze disparate security data widely dispersed throughout the enterprise stack.
Graph theory provides a mathematical approach to parsing data for the benefit of enhanced security. It offers the ability to model relationships between objects while laying out the enterprise security stack in properties and graph visualizations. More importantly, it provides a relevant, context-based approach to understanding security events by decomposing components of observable data into a graph.
These graphs are very useful in helping us understand vulnerabilities by visualizing relationships of artifacts across data elements and preserving them in their present and past historical contexts.
A constantly evolving attack landscape requires actionable CSPM solutions that can dynamically identify threats in real-time. But no matter how well-guarded a network appears to be, its complex interdependencies provide attackers with the upper-hand in subverting the system through multi-step attacks.
When used in isolation, both attack and dependency graphs have proven insufficient for accurately assessing an attack’s impact. The missing ingredient in the equation is lack of context in prioritizing risks.
Context helps provide DevSecOps with an accurate, realistic picture of their current threat environment. A multi-layered CSPM solution equipped with prioritization engines is capable of filtering out trivial alerts and clearing the white noise generated by noncritical misconfiguration alerts.
This well-rounded context subsequently frees DevSecOps to focus on meaningful threats and vulnerabilities. With this scenario, attack graphs become even more relevant to DevSecOps, providing them a unified view of their networks with real, actionable remediation guidance to address the most critical problems.
In this era of countless vulnerabilities and complex interdependencies among cloud entities, businesses need to have far-reaching visibility inside their networks to successfully identify and thwart threats. This requires a CSPM solution that combines attack-path analysis and advanced graph theory algorithms to visualize, prioritize, and remediate threats.
Panoptica has experience modeling possible attack paths with its graph and context-based cloud security. Try Panoptica’s free demo today.